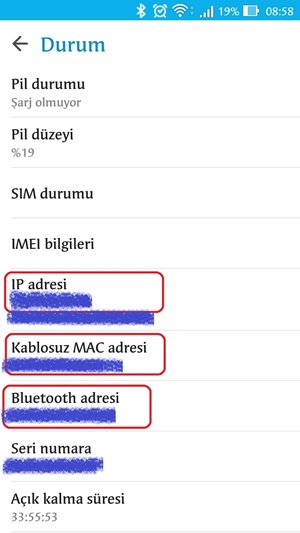
Android telefonun mac adresini bulma
This fake AP attack will cause any nearby device which has connected to a network with the same name SSID before to attempt to connect, revealing its true MAC address and populating a list of open essentially the device trusts. This information allows an attacker to use these trusted open networks stored on the phone to unmask or connect to the target's device at will, simply by creating a fake AP with the same name and preventing the victim from connecting to other networks. Once these network names are identified, the attacker can use these them to take over the victims data connection with a MITM attack without any warning or prompt on the device.
We made the assumption that the most popular SSIDs are open hotspots that do not use encryption. Therefore, the APs we broadcast were configured to be open hotspots. Therefore, we limited our attack to a reasonable number of SSIDs, i.
- BiP, her şeyiyle bizim, her şeyiyle Türkiye’nin yerli uygulaması!.
- Sayfa Sonu Bağlantıları.
- Vodafone Yeni Cepnet Paketleri;
- flight simulator rc mac os x;
- convert jpg to doc mac?
- belkin nostromo n52 drivers mac;
By using a modified version of Spacehuhn's Beacon Spammer, we're able to raise the number of advertised SSIDs to hundreds, improving our chances of finding trusted networks saved on nearby devices. This means swarming devices with hundreds of popular SSIDs may be overkill, but it should work just fine. It's also worth noting that this behavior isn't only seen when an attacker is behind it.
Walking by any business with a popular SSID like a coffee shop you've connected to before will also cause your device to attempt to connect and drop its fake MAC address. Usually, this means you're stuck with no data until you notice you've been connected automatically and sign into the network. An attacker set up near a real network which has a common SSID can also take advantage of this to track users passing nearby, without needing to do the work of creating a fake network themselves. These IoT development boards are cheap and easy to program and work with. You can pick up a generic one or grab one of the official boards from Spacehuhn.
For watching and understanding what's happening, we'll be using Wireshark , which is cross-platform and included in Kali Linux. You'll want to make sure that you pick SSIDs that are common in your area, as this attention to detail will improve your results.
Find Your Router’s IP Address in Windows
In this guide, we will use the free and cross-platform Arduino IDE , which will allow us to quickly prototype what we need. Arduino IDE the IDE stands for "integrated development environment" allows you to quickly write and upload scripts to Arduino-like microcontroller devices. You can download the Arduino IDE from the official website.
Once it's installed, you'll need to click on the "Arduino" drop-down menu, then select "Preferences. Click on "Tools," then hover over the "Board" section to see the drop-down list. At the top, click "Boards Manager" to open the window that will allow us to add more boards.
When the Boards Manager window opens, type "esp" into the search field. Select "esp" by "ESP Community," and install it. You should be ready to program your NodeMCU at this point. Plug in your breadboard to your computer, which should have the NodeMCU already attached. When you click on "Tools," you should see the correct port auto-selected. Select the "NodeMCU 1. If you're using a bad cable, the port may not show up, so if you don't see anything after you've completed the other steps, try another cable first. There are two main buttons up top. The check mark compiles and checks our code for mistakes, and the right arrow pushes the code to the NodeMCU.
Next, we'll need to download SpaceHuhn's Beacon Spammer project. This project is just one of the awesome things Stefan has created, including these awesome boards with the software preinstalled. Some of these designs also have support for adding custom antennas, so it's worth taking a look at the hardware side of the project as well.
If you're interested in seeing more of Stefan's projects, see his website. The preinstalled networks have some pretty amazing SSID's installed, but they won't work for our purposes. First, we'll need to create a list of network names that we believe nearby devices will respond to. For beacon swarming attacks, the best results come from open no password SSIDs that are common in the area. If you have an Android phone, you can use Wigle Wifi to walk or drive around your city to collect wireless network names to broadcast. Next, take the resulting CSV file, and load it onto your computer.
Open it in Excel or Google sheets, and then order the list by encryption type or "AuthMode. Copy all these network names to a list, and you may see many duplicates. To fix this, save them to a text file, and then run the following script to order them by frequency and eliminate duplicates. If you have a list of SSIDs you want to add to the code, you can use the Python script I wrote to format it with the quotes around it and newline character needed by the Beacon Spammer script so that you can just drop it into the program.
Add as many network names as you want in a. Remember to change "inputfile" to the location of the. Now, you can take the network names and drop them into the part of the beacon spammer script that lets you list the networks to create. Here's a list I made for Southern California:. We will need to modify the default settings for the Beacon Spammer to ensure the behavior we want. To do this, we'll refer to the handy configuration settings in the beginning of the code in the.
- chrome internet explorer compatibility mode mac!
- counter strike online free download for mac.
- sync ipod to new mac computer without losing songs?
INO file we downloaded earlier. To be able to keep track of the replies to our fake networks, reduce the number of channels to broadcast on to just one channel. You can pick whichever channel you want, but if you're broadcasting on multiple channels, you won't be able to keep track of devices replying to the fake networks. Some research suggests channel 4 is the best channel for this.
Wifi Şifre Kırıcı
This will cause devices to see our fake networks as "open" networks with no password. Next, SpaceHuhn added a handy option to let our attack work by disabling a feature that makes all SSIDs the same length. Change "appendspaces" to false so that SSIDs we put in our list will be exactly the same as the ones broadcast by the Beacon Spammer. If you forget to do this, the networks it creates will be seen as not matching any SSIDs stored in nearby devices because the length will always be set to 32 characters.
Your modified code should look like below. Next, you'll need to open Wireshark and prepare to watch for responses to our "bait" networks. I've set mine to broadcast on channel 1, so in Wireshark, we'll need to be sure we're watching for traffic on the same channel. If you're on Kali Linux, select the network adapter you'll be using from the list of availible network interfaces you see after running ifconfig.
Tenorshare Android Data Recovery
Next, run the following command to put your network adapter into monitor mode and set the channel to 1. Your card should be named something like wlan0 or wlan1. My server is hosted by 1and1 so this will be unreliable if you use the same DNS servers. Hostname L ' is the hostname your device resolves your external IP local resolve. Hostname R ' is the hostname my server resolves your external IP remote resolve.
The menu item will only appear if the 'Field Test' is installed in your phone. This is a problem in Samsung's Android implementation and there is nothing I can do. No other information is logged or kept. I cannot reply to market comments which can make debugging difficult. Reklam yok. Added Interfaces Tab which will contain information about all interfaces. The application will now hide tabs pertaining to capabilities a device does not have. Users can now hide tabs they do not need via the Preferences. Refactoring Gallore. Web sitesini ziyaret edin. Network Cell Info Lite. Fing - Network Tools.
Fing Limited. Network Analyzer Pro. Jiri Techet.
Network Analyzer.