Cisco switch restrict port mac address
See the " Configuring Port Security " section. To ensure that an attached device has the full bandwidth of the port, set the maximum number of addresses to one and configure the MAC address of the attached device. You probably will want to look into port-security sticky dynamically learns the MAC then configure aging to age out old MAC Addresses on each interface. You wont be able to have port security configured and at the same time allow a MAC to move from interface to interface without problems.
- add photo to folder icon mac.
- Prerequisites for Port Security!
- my internet sound is not working mac.
As stated above, it defeats the purpose of port-security. When you set your aging parameters you have several options, you can have it based on time, or type, or statically set:.
Catalyst 4500 Series Switch Cisco IOS Software Configuration Guide, 12.2(25)EW
Like Ron says in his response, you will want to have port-security to dynamically learn sticky the MAC addresses, possible set a max amount to learn on each interface, and configure the aging parameters to what best suits you. By clicking "Post Your Answer", you acknowledge that you have read our updated terms of service , privacy policy and cookie policy , and that your continued use of the website is subject to these policies.
Home Questions Tags Users Unanswered. How can I allow the same MAC address on different ports with port security? Ask Question. How can I allow my laptop MAC address on every port with port security? Is it even possible? When I try, I get this: Tech Tech 88 2 Please allow me to join the discussion. That defeats the purpose of one aspect of port security: This aspect of port security prevents that from happening. Port Security: If you do not save the configuration, they are lost.
Restrictions for Port Security
If sticky learning is disabled, the sticky secure MAC addresses are converted to dynamic secure addresses and are removed from the running configuration. After the maximum number of secure MAC addresses is configured, they are stored in an address table. To ensure that an attached device has the full bandwidth of the port, configure the MAC address of the attached device and set the maximum number of addresses to one, which is the default.
Note When a Catalyst series switch port is configured to support voice as well as port security, the maximum number of allowable MAC addresses on this port should be changed to three.
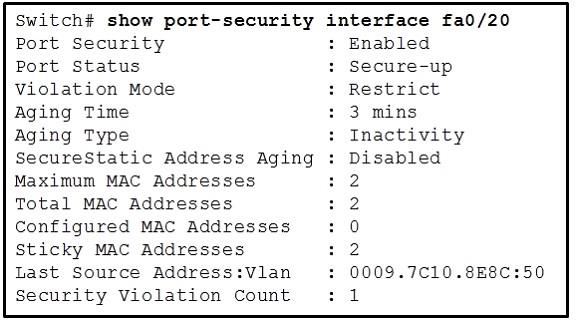
A security violation occurs if the maximum number of secure MAC addresses has been added to the address table and a workstation whose MAC address is not in the address table attempts to access the interface. You can configure the interface for one of these violation modes, based on the action to be taken if a violation occurs:. The rate at which SNMP traps are generated can be controlled by the snmp-server enable traps port-security trap-rate command.
The default value "0" causes an SNMP trap to be generated for every security violation. When a secure port is in the error-disabled state, you can bring it out of this state by entering the errdisable recovery cause psecure-violation global configuration command or you can manually reenable it by entering the shutdown and no shut down interface configuration commands.
This is the default mode. You can also customize the time to recover from the specified error disable cause default is seconds by entering the errdisable recovery interval interval command.
To restrict traffic through a port by limiting and identifying MAC addresses of the stations allowed to access the port, perform this task:. Sets the interface mode as access; an interface in the default mode dynamic desirable cannot be configured as a secure port. Optional Sets the maximum number of secure MAC addresses for the interface. The range is 1 to ; the default is 1. Optional Sets the violation mode, the action to be taken when a security violation is detected, as one of these:. Note When a secure port is in the error-disabled state, you can bring it out of this state by entering the errdisable recovery cause psecure-violation global configuration command or you can manually reenable it by entering the shutdown and no shut down interface configuration commands.
Optional Enters a secure MAC address for the interface. You can use this command to enter the maximum number of secure MAC addresses. The interface converts the sticky secure MAC addresses to dynamic secure addresses. To delete all the sticky addresses on an interface or a VLAN, use the no switchport port-security sticky interface interface-id command.
The address keyword enables you to clear a secure MAC addresses.
Limit ports access for particular MAC a - Cisco Community
The interface keyword enables you to clear all secure addresses on an interface. This example shows how to enable port security on Fast Ethernet port 12 and how to set the maximum number of secure addresses to 5. The violation mode is the default, and no secure MAC addresses are configured. You can use port security aging to set the aging time and aging type for all secure addresses on a port. Use this feature to remove and add PCs on a secure port without manually deleting the existing secure MAC addresses while still limiting the number of secure addresses on a port.
Enters interface configuration mode for the port on which you want to enable port security aging. If you limit the number of allowed MAC addresses allowed on a port to only one MAC address, only one device will be able to connect to that port and will get the full bandwidth of the port.
- gears of war 3 for mac download.
- x lite voip download mac.
- hotmail icon on mac desktop.
- mac duna make it work lyrics.
- raw therapee ita download mac;
If the maximum number of secure MAC addresses has been reached, a security violation occurs when a devices with a different MAC addresses tries to attach to that port. A switch can be configured to only protect or restrict that port.
Lock down Cisco switch port security
We will discuss theses security violation modes a little bit later. In a Cisco switch, you are able to configuration three types of security violation modes. A security violation occurs when the maximum number of MAC addresses has been reached and a new device, whose MAC address is not in the address table attempts to connect to the interface or when a learned MAC address on an interface is seen on another secure interface in the same VLAN.
Depending on the action you want a switch to take when a security violation occurs, you can configure the behavior of a switch port to one of the following:. The default configuration of a Cisco switch has port security disabled. If you enable switch port security, the default behavior is to allow only 1 MAC address, shutdown the port in case of security violation and sticky address learning is disabled. Next, we will enable dynamic port security on a switch. As you can see, we did not specify an action to be taken if a security violation occurs, neither how many MAC addresses are allowed on the port.
Recalling from above, the default behavior is to shutdown the port and allow only one MAC address. If a violation occurs, you want the port to be configured in restrict mode.